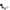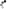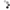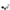The USB armory Mk II is a full featured computer (900 MHz ARM® processor, 512 MB RAM, Bluetooth, USB-C) in a tiny form-factor, designed from the ground up with information security applications in mind.
Hardware:
- SoC: NXP i.MX6ULZ ARM® Cortex™-A7 900 MHz
- RAM: 512 MB DDR3
- Storage: internal 16 GB eMMC + external microSD
- Bluetooth module: u-blox ANNA-B112 BLE
- USB-C ports: DRP (Dual Role Power) receptacle + UFP (Upstream Facing Port) plug, USB 2.0 only (no video support)
- LEDs: two
- Slide switch: for boot mode selection between eMMC and microSD
- External security elements: Microchip ATECC608A + NXP A71CH
- Physical size: 66 mm x 19 mm x 8 mm (without enclosure, including USB-C connector)
- Enclosure: included with all units for device protection
Software:
The USB armory Mk II hardware is supported by standard software environments and requires very little customization. In fact, vanilla Linux kernels and standard distributions run seamlessly on the tiny board:
- Boots from on-board eMMC or microSD (or via USB serial downloader)
- Native Linux support - creating boot images is easy
- Precompiled images are available for Debian 9 (Stretch) and Arch Linux, with more on the way
- USB device emulation (CDC Ethernet, mass storage, HID, etc.)
Connectivity:
- USB 2.0 over USB-C plug to host with full device emulation
- USB 2.0 over USB-C receptacle for the additional devices or as a connection to host
- Full TCP/IP connection to/from USB armory via USB CDC Ethernet emulation
- Flash drive functionality via USB mass storage device emulation
- Serial communication over USB or physical UART using the Debug Board
- Wireless connectivity over BLE
Note: only the USB 2.0 protocol is supported over both USB-C ports, therefore it should be emphasized that HDMI video over USB-C is not supported.
Applications:
The following example security application ideas illustrate the flexibility of the USB armory Mk II concept:
- Mass storage device with advanced features such as automatic encryption, virus scanning, host authentication, and data self-destruct
- Hardware Security Module (HSM)
- OpenSSH client and agent for untrusted hosts (e.g., Internet kiosks)
- Router for end-to-end VPN tunnelling
- Tor bridge
- Password manager with integrated web server
- Electronic wallet
- Authentication token
- Portable penetration testing platform
- Low-level USB security testing
Security Features:
- High Assurance Boot (HABv4)
- True Random Number Generator (TRNG)
- Data Co-Processor (DCP)
- Secure Non-Volatile Storage (SNVS)
- ARM® TrustZone®
- External cryptographic co-processors (ATECC & A71CH)
- eMMC Replay Protected Memory Blocks (RPMB)
High Assurance Boot (HABv4):
The HAB feature enables on-chip internal Boot ROM authentication of the initial bootloader (i.e., Secure Boot) with a digital signature, establishing the first trust anchor for code authentication. See Secure Boot for more information and usage instructions.
True Random Number Generator (TRNG):
The RNGB driver is included and operational in modern Linux kernels. Once loaded, it enables the component within the Linux hw_random framework.
Data Co-Processor (DCP):
From the i.MX6ULZ datasheet:
This module provides support for general encryption and hashing functions typically used for security functions.
The DCP module driver is included and operational in modern Linux kernels. Once loaded, it exposes its algorithms through the Crypto API interface.
Secure Non-Volatile Storage (SNVS):
From the i.MX6ULZ datasheet:
Secure Non-Volatile Storage, including Secure Real Time Clock, Security State Machine, Master Key Control, and Violation/Tamper Detection and reporting.
A device-specific random 256-bit OTPMK key is fused in each SoC at manufacturing time. This key is unreadable and can only be used by the DCP for AES encryption/decryption of user data, through the Secure Non-Volatile Storage (SNVS) companion block.
ARM TrustZone:
The i.MX6 SoC family features an ARM® TrustZone® implementation in its CPU core and internal peripherals. From the ARM® website:
At the heart of the TrustZone® approach is the concept of secure and non-secure worlds that are hardware separated, with non-secure software blocked from accessing secure resources directly. Within the processor, software either resides in the secure world or the non-secure world; a switch between these two worlds is accomplished via software referred to as the secure monitor.
This concept of secure (trusted) and non-secure (non-trusted) worlds extends beyond the processor to encompass memory, software, bus transactions, interrupts, and peripherals within an SoC.
External cryptographic co-processors (ATECC & A71CH):
The Microchip ATECC608A and NXP AT71CH feature hardware acceleration for elliptic-curve cryptography, as well as hardware-based key storage. The ATECC608A also features symmetric AES-128-GCM encryption. Both components provide high-endurance monotonic counters, useful for external verification of firmware downgrade/rollback attacks. Both components communicate on the I²C bus and feature authenticated and encrypted sessions for host communication.
eMMC Replay Protected Memory Blocks (RPMB):
The eMMC RPMB features replay-protected authenticated access to flash memory partition areas, using a shared secret between the host and the eMMC.
Communication Interfaces:
USB:
USB armory Mk II features two USB-C ports. Using USB-C allows us to have a plug for traditional USB-based host communication, along with an integrated receptacle to act as a host (or device).
The USB-C current mode ensures that adequate current is requested on the plug side, to enable connection of additional devices on the receptacle side. This design enables new use cases for the USB armory Mk II. It can act as a USB firewall without the need for additional hardware, and it can be natively expanded with USB peripherals (e.g., storage and network adapters).
Additionally, the integrated receptacle also allows its role to be changed to device, simplifying scenarios such as controlled USB fuzzing from one side and interactive console/control on the other.
Only the USB 2.0 protocol is supported over both USB-C ports, therefore it should be emphasized that HDMI video over USB-C is not supported.
Bluetooth:
The Mk II includes a u-blox ANNA-B112 Bluetooth module for out-of-band (in relation to USB interfaces) interaction with a wireless client (e.g., mobile applications).
The addition of a Bluetooth module opens up a variety of new use cases for the USB armory Mk II, greatly enhancing its security applications in terms of authentication, isolation, and limiting trust of the host.
The ANNA-B112 module supports an "OpenCPU" option to allow arbitrary firmware, replacing the built-in u-blox firmware, on its Nordic Semiconductor nRF52832 SoC. This allows provisioning of the SoC with Nordic SDK, Wirepas mesh, ARM® Mbed, or arbitrary user firmware. The nRF52832 SoC features an ARM® Cortex-M4 CPU with 512 KB of internal Flash and 64 KB of RAM.
Storage Media:
Apart from the traditional microSD slot (now with a spring-loaded push-to-insert, push-to-eject mechanism), the USB armory Mk II includes a 16 GB eMMC flash memory chip on the board.
This makes provisioning easier, allows for factory pre-imaging without the burden of microSD card installation, and enables additional security features.
Additionally a slide switch allows selection of the boot mode (microSD vs eMMC), which makes it easy to select the boot media for dual boot purposes (e.g., full Linux OS vs INTERLOCK protected image).
Comparing Mk I and Mk II:
| USB armory Mk II | USB armory Mk I | |
| HARDWARE | ||
| SoC | NXP i.MX6ULZ ARM® Cortex™-A7 | Freescale i.MX53 ARM® Cortex™-A8 |
| Operating frequency | 900 MHz | 800 MHz |
| RAM | 512 MB | 512 MB |
| On-board storage | 16 GB eMMC | None |
| External storage | microSD | microSD |
| Wireless capabilities | Bluetooth 5, BLE, BT Mesh | None |
| Host connector (USB 2.0) | USB-C | USB A |
| Peripheral connector (USB 2.0) | USB-C | USB A via external adapter |
| LEDs | 2 | 1 |
| GPIO | 8 via Debug Board | 5 on board |
| GPIO interfaces | UART, SPI, I²C | UART, SPI, I²C |
| SECURITY | ||
| Open hardware | Yes | Yes |
| Secure Boot | HABv4.2.6 | HABv4.0.4 (insecure) |
| True Random Number Generator | Yes | Unsupported |
| SoC cryptographic acceleration | DCP | SAHARAv4 Lite |
| Secure storage handling | SNVS | SCCv2 |
| ARM® TrustZone® | Yes | Yes |
| External cryptographic co-processors | ATECC & A71CH | No |
| Protected flash memory region | RPMB | No |
USB armory Mk II Debug Board:
The USB armory Mk II exposes a USB-C receptacle, which allows the so-called ‘debug accessory mode’ to route analog/debug signals over its connector. The USB armory Mk II design leverages this to break out UART, SPI, I²C, and GPIO connections to/from its application processor.
The debug accessory board allows access to UART and GPIO signals through USB, without requiring probes, through an FTDI FT4232H. This allows, for example, access to the USB armory Mk II serial console without wires or probes, natively using only USB cables. All other interfaces can be accessed through dedicated breakout through-holes.
The board measures 22 mm x 57 mm x 12 mm, including the length of the USB-C connector.
Enclosure:
To keep your USB armory Mk II protected and preserved, we’ve developed a custom enclosure in cooperation with TEKO, an Italian company that specializes in high-quality enclosures.
The enclosure provides proper access to the USB-C ports as well as the microSD card slot and boot-select switch. It also features a slot for attaching a lanyard.
32 GB microSD Card w/ Debian Image:
A 32 GB microSD card pre-imaged with Debian. USB armory Mk II has a built-in flash, which is unprovisioned by default, so a microSD is not strictly necessary for booting an OS.
Package Includes:
- A tiny, open source USB computer in an injection-molded enclosure with onboard i.MX6ULZ 900 MHz processor and 512 MB RAM.
USB armory Mk II with Enclosure
- Brand: Crowd Supply
- Product Code: CS-USB-armory-Mk-II
- Reward Points: 203
- Availability: In Stock
-
रo 20,272.00
- Price in reward points: 20272
-
- 2 or more रo 19,063.00
- 3 or more रo 18,562.00
- 6 or more रo 18,067.00
Available Options
Related Products
SyncStop - USB Lock
SyncStop prevents accidental data exchange when your device is plugged into someone else’s computer ..
रo 1,825.00
The Original USB Condom
The Original USB Condom prevents accidental data exchange when your device is plugged into a foreign..
रo 562.00
Faulty Cat
Faulty Cat is an Electromagnetic Fault Injection (EMFI) tool, designed specifically for self-study a..
रo 17,916.00